
- About
- Courses Library
- Live programs
Network Cyber Course
- Live programs
- Services
- Skill Mapping
- Contact Us
G One Training Centre has been formed by a number of training professionals who have operated in the UAE and GCC for a number of years. Together we have one common goal; the development of individuals, teams and organizations within Government, the Military, and Commercial sectors through the development of cost-effective training programs that are tailored to meet the needs of an organization, yet flexible enough to meet their changing operational environment. Our core consultants, together with supporting facilitators and other staff, work together in various specialized areas to bring a wide range of experience to our clients.
Our staff have several years’ experience delivering training to customers in the UAE. With regard to the delivery of many programs from individual programs, in addition to the “System Approach to Training” (SAT) program, our team has over 5 years’ experience delivering SAT.
The National Institute of Standards and Technology (NIST) provides a library of resources to help organizations and government agencies build cybersecurity awareness and training programs to educate employees and keep their organizations secure.
This program powered by “Infosec IQ” this security awareness and training program is built in accordance with these guidelines to help you stay compliant and empower your employees with the knowledge and skills to stay cyber secure.
Cybersecurity training for all employees covering the following topics:
This cybersecurity awareness program provides your teams with the step-by-step guidance they need to keep themselves, their data, and your organization safe from cyber criminals.
The core of this program is our award-winning series of instructional modules. Hosted by cybersecurity expert” Keatron Evans” and his team, Just the Facts covers the key cybersecurity topics recommended by The National Institute of Standards and Technology (NIST). Each module explores one common threat vector and provides step-by-step instructions on how to recognize and defend against such a threat.
These modules are short (around five minutes long), straightforward and concise - giving your team the most efficient and effective training possible.
The program includes twelve training sessions, each containing one live action module and a ten questions assessment based on the module topic. Each session is supported by a dedicated PhishSim template battery (with a unique Education page), a poster, and an infographic.
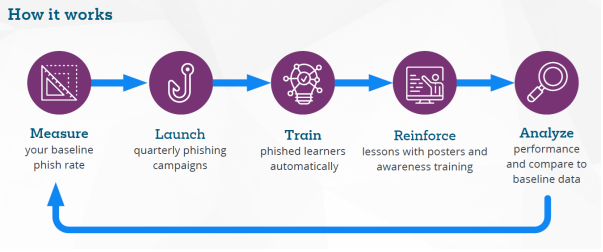
12 live action training modules: Assign themed training modules covering the cybersecurity topics recommended by NIST.
12 assessments: Test employee knowledge and lesson retention with assessments for each core cybersecurity topic.
29 phishing templates: Watch employee behaviour change with phishing templates simulating the topics and attacks covered in the training materials.
12 phishing education pages: Tie anti-phishing training to your awareness campaign with phishing education pages themed to our Just the Facts modules.
12 posters: Hang posters in common areas and high traffic locations to extend your campaign communication offline.
Take a closer look at each cybersecurity topic with topical data and visual examples.
By the end of the training, participants will enable to:
Understand the cybersecurity fundamentals
Understand how to mitigate risks to sensitive information
understanding of security and data protection methods, resources, and processes for using computers, software and online applications
Understand the cybersecurity fundamentals
Understand how to mitigate risks to sensitive information
understanding of security and data protection methods, resources, and processes for using computers, software and online applications
MALWARE: Malware can hide in almost any website, email, or app. In this session, learn what malware is, how it gets into your computer and how to prevent it.
MOBILE SECURITY: With smartphones and laptops, you can take work anywhere. But how do you keep your device safe? This session highlights the steps you can take to secure both your device and your data.
SAFE WEB BROWSING: The internet is full of malicious websites designed to trick you. This session identifies the most common warning signs and details how to stay safe when exploring the web.
PHISHING: Phishing emails disguise themselves as legitimate messages. So, how do you tell which ones are real and which ones are malicious? This session covers the most common phishing attacks and how you can identify them.
REMOVABLE MEDIA: USB drives are small, portable, and convenient … but they also pose a big security risk. This session highlights the risks of using unencrypted media, as well as the dangers of found media.
PUBLIC WI-FI: You just connected to a public Wi-Fi network, but is it real or fake? Even if it is real, is it safe? In this session, learn how to use public Wi-Fi safely.
PASSWORD SECURITY: Passwords are the key to your entire digital life. This session will teach you the most current techniques to help you create and maintain strong passphrases.
SOCIAL ENGINEERING: Social engineering doesn’t rely on a computer’s weakness. It relies on human kindness. This session identifies the most common ways social engineers manipulate you into giving them information — and what you can do to stop them.
WORKING REMOTELY: Today, more people than ever are working from home. But just because it’s easy, that doesn’t mean it’s safe. In this session, learn how to set up and secure your remote workspace.
RANSOMWARE: Your computer is locked. Your data is being held captive. What do you do? This session shows you how to deal with a ransomware attack and the steps you can take to avoid them in the future.
PHYSICAL SECURITY: Good cybersecurity doesn’t work if someone can walk in and steal your computer. In this session, learn how to secure your physical environment as well as your digital devices.
DATA PRIVACY: Revealing someone’s personal data, even accidentally, may violate numerous laws and result in huge fines. This session will show you how to properly identify, handle and protect sensitive data in your possession.